No Updates, No Cry?
"For the Windows OS to run smoothly, all system updates must be installed." You may have heard this phrase a thousand times, but what does it really mean? For us, as software developers, it goes down to concrete things.
Before We Start
Let's go ahead and briefly review why you need to keep Windows up to date.
- Security: Protect your system from vulnerability exploit attacks by applying the latest security patches. Also, by updating, you ensure ongoing support from the Microsoft side.
- Stability: Updates often include bug fixes and performance improvements that can help prevent crashes, freezes, and other issues that affect the system's stability.
- Compatibility: compatibility with new software and hardware components and top-notch cloud services.
- New features: Updates often also introduce new OS features and capabilities. These may improve productivity, enhance security, or provide new user functionality.
- Regulatory compliance: In some industries, there are regulatory requirements that mandate the use of updated software to ensure compliance. Failure to comply with these requirements can result in fines, legal penalties, or other negative consequences.
- Avoid downtime: Installing updates takes less time than handling the results of an exploited security flaw or a compatibility issue and does not involve lost productivity, revenue, and customer satisfaction.
Let's take a closer look at one specific aspect of one of these reasons — security certificates — and explore how you can address this issue on your server if it doesn't have access to Windows updates.
How They Work
Essentially, security certificates are digital files that verify a website's or software application's authenticity. As you surf, play games, or use software, certificates help you access legitimate content without being redirected to fake or malicious sites. In other words, certificates help establish trust between you and the target software (local or remote), ensuring that a third party does not access or modify the data.
Most of the time, all those security checks happen automatically. You will notice they happen when something goes wrong. Like, your browser won't connect you to a site that has an expired certificate.
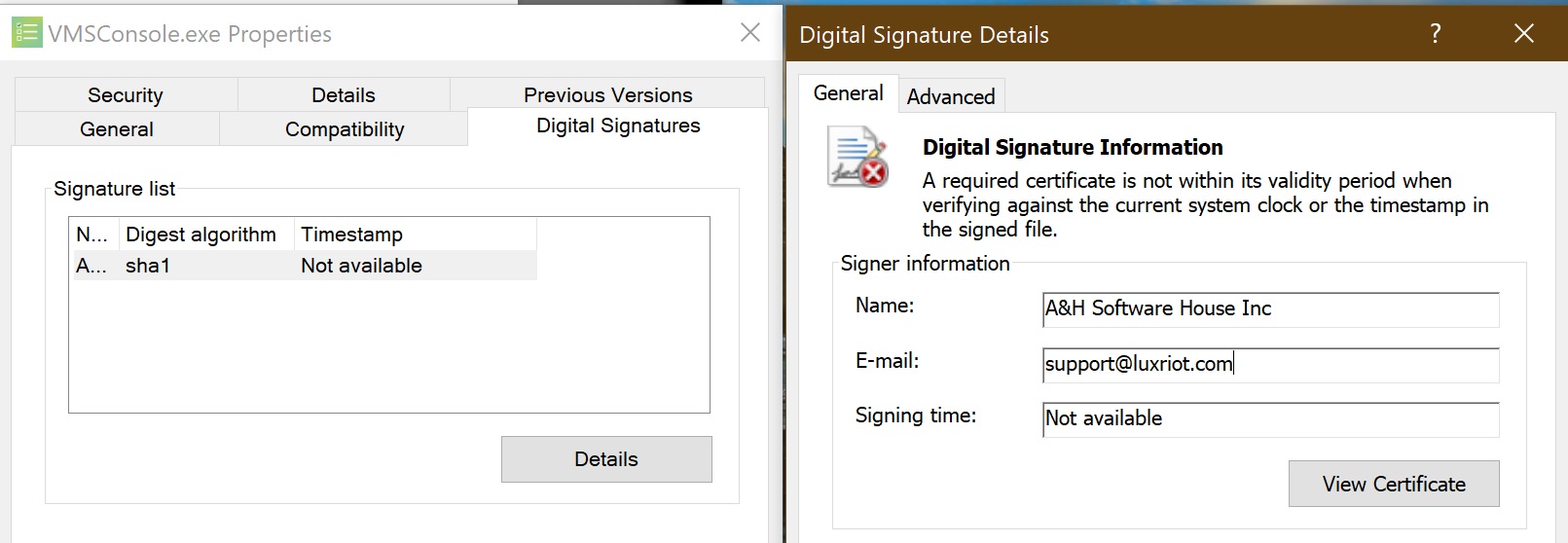
An example of an invalid software certificate
In terms of Evo software, it is all the same. If you keep your OS up to date and download the software from the official website, everything will be smooth and silent. Meanwhile, what happens in the background:
- We sign Evo software with a Code Signing Certificate issued by a certification authority. Each certificate is valid for a specific period.
- Your OS must know about those newly issued certificates. Otherwise, it will be unable to trust the certificate inside the new software version.
- When Windows downloads updates, it also receives the latest information about the released trusted certificates.
And What if They Don't
Thus, issues may arise when
- the next software version is signed with a new certificate, which is not present in the trusted certificate list on the local machine >> you won't be able to install the latest software version; or
- your OS root certificate expires >> all certificates validated by it are not trusted anymore >> the already running software will stop operating.
In the first case, you will immediately know about the problem when starting the installation. Or even not know about it at all if the computer is connected to the internet, as the OS will download the required certificate on demand. The second case poses a more serious issue, as you will not get any notifications about the situation.
How Will You Know
How can you find out if there is an issue with the Evo certificate? A typical symptom is that your Evo clients won't connect to the server, as if it does not exist or is not running at the target address. Of course, this behavior is also typical when Evo services are stopped, so, first of all, verify that the services are running and that you are using the correct addresses. Next, run the netstat command from the Windows Command Line: your Evo TCP and HTTP/HTTPS ports (60554 and 8080 by default) must be LISTENING.
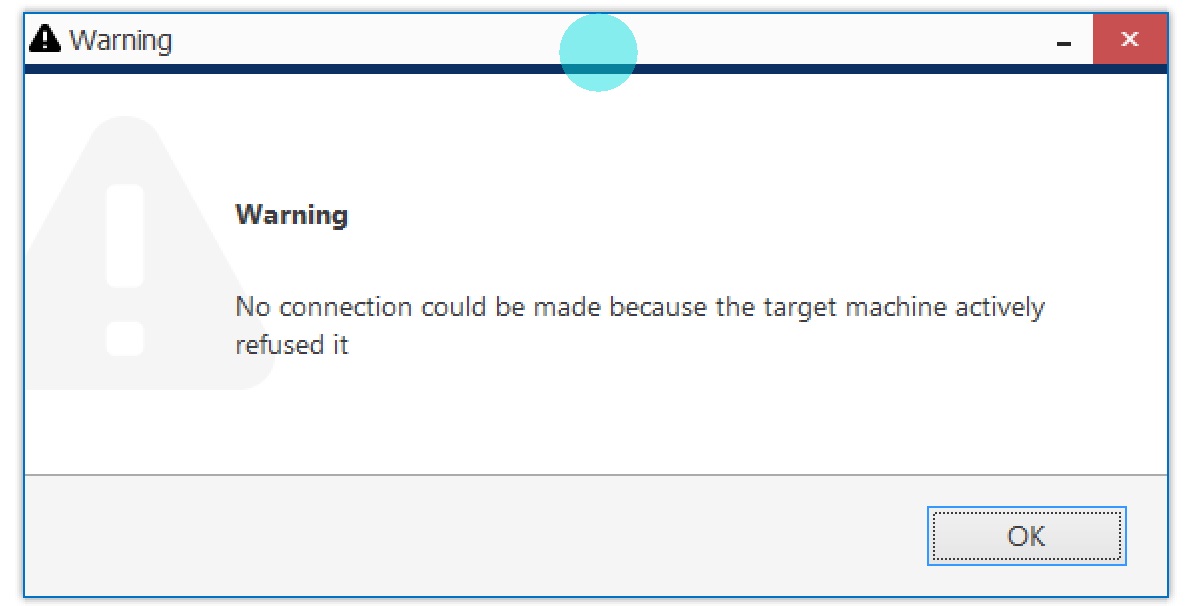
Evo Console error message that shows when you try connecting to a non-existent service
So, again, if the troubleshooting reveals that
- Evo services are up and running, but Evo server ports are not open, and
- as a result, upon connection attempt, Evo Console/Monitor produces the "No connection could be made because the target machine actively refused it" error (even if it should be another error, e.g., wrong password), and
- when you check the digital signature in the properties of the Evo .exe files, you see that Windows cannot validate the certificate,
the certificate is likely causing the problem.
And How to Fix
Option 1: If a newer software version exists, you can just install it and see if it helps. However, if the certificate is valid (not outdated), the next version will likely use the same one.
Option 2: downgrade to the previous software version. This may serve as a temporary fix if you need the newest Evo features.
Option 3: Install the required certificates. If you want to avoid receiving regular OS updates automatically, you must manually update the certificates as described below. The general plan is to use a computer with Internet access to download the full list of current root certificates, then install the certificates from that file on the offline server.
Download
On a computer with Internet access (e.g., your laptop), use certutil.exe — a CLI tool built into Windows 10 and 11 and a part of Certificate Services in Windows Server — for certificate management. To generate the file, open the command prompt with elevated rights (cmd.exe >Run As > Administrator) and type:
C:\Windows\System32>certutil.exe -generateSSTFromWU C:\roots.sst
where C:\roots.sst is the path to the SST file to be generated. If you put it into a directory, ensure the folder exists — otherwise, you will get an error like the one shown in the snapshot. You can also first navigate to the target directory and then use the command without the path parameter.
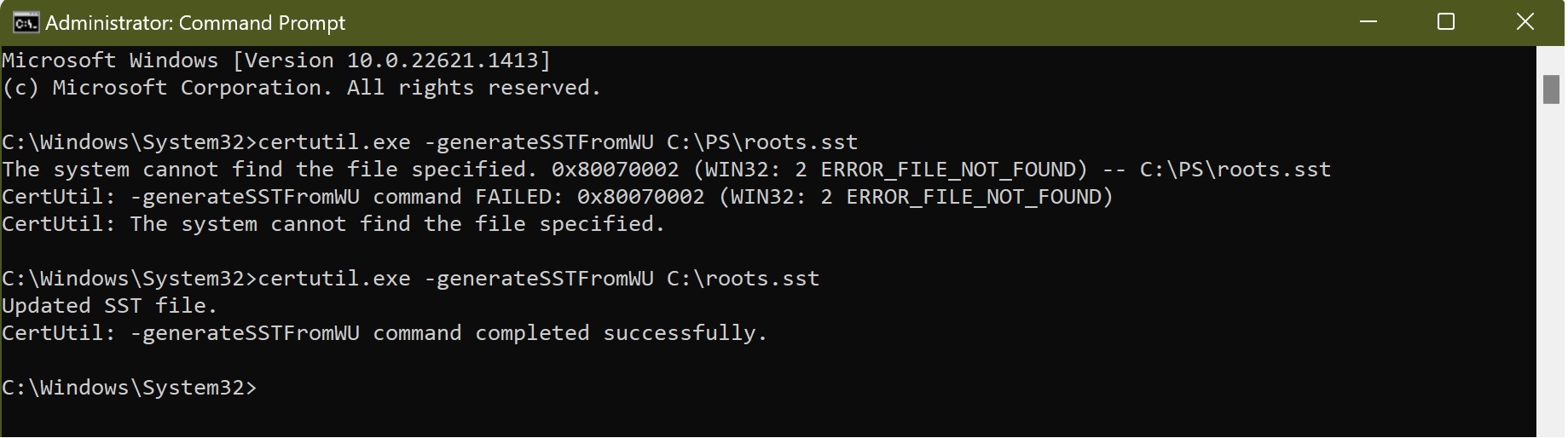
Use cmd to generate the certificate container file
Import
Copy the SST file to the server that doesn't have the updates and Internet access, and do the following there:
- Click Start > Run (or Win key +R) to open the prompt window, then type certmgr.msc to open the certificate manager (alternatively, type certmgr in the Windows search panel and open the certificate management).
- Right-click the "Trusted Root Certification Authorities" node > All Tasks > Import.
- In the wizard, click Next > Browse for files > change the target file type to "All Files" to include the SST file type > select your imported SST file.
- Choose the "Place all certificates in the following store" option, where "Trusted Root Certification Authorities" should be pre-specified (see snapshot).
- Click Next to proceed, then click Finish.
You will have to click the confirming "Yes" a lot of times times, once for every certificate in the .sst file. At that point, you will probably swear to enable automatic updates the next thing.
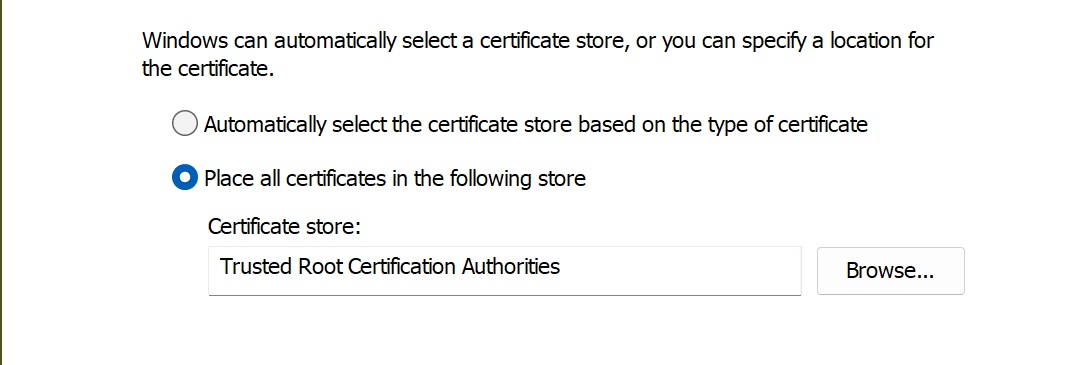
Step 4: ensure you are installing the certificates into the correct destination
Luckily, there is a much quicker way to do import the whole lot — by using the Windows PowerShell with the following commands (remember to adjust the file path according to yours):
$sstStore = ( Get-ChildItem -Path C:\roots.sst )
$sstStore | Import-Certificate -CertStoreLocation Cert:\LocalMachine\Root
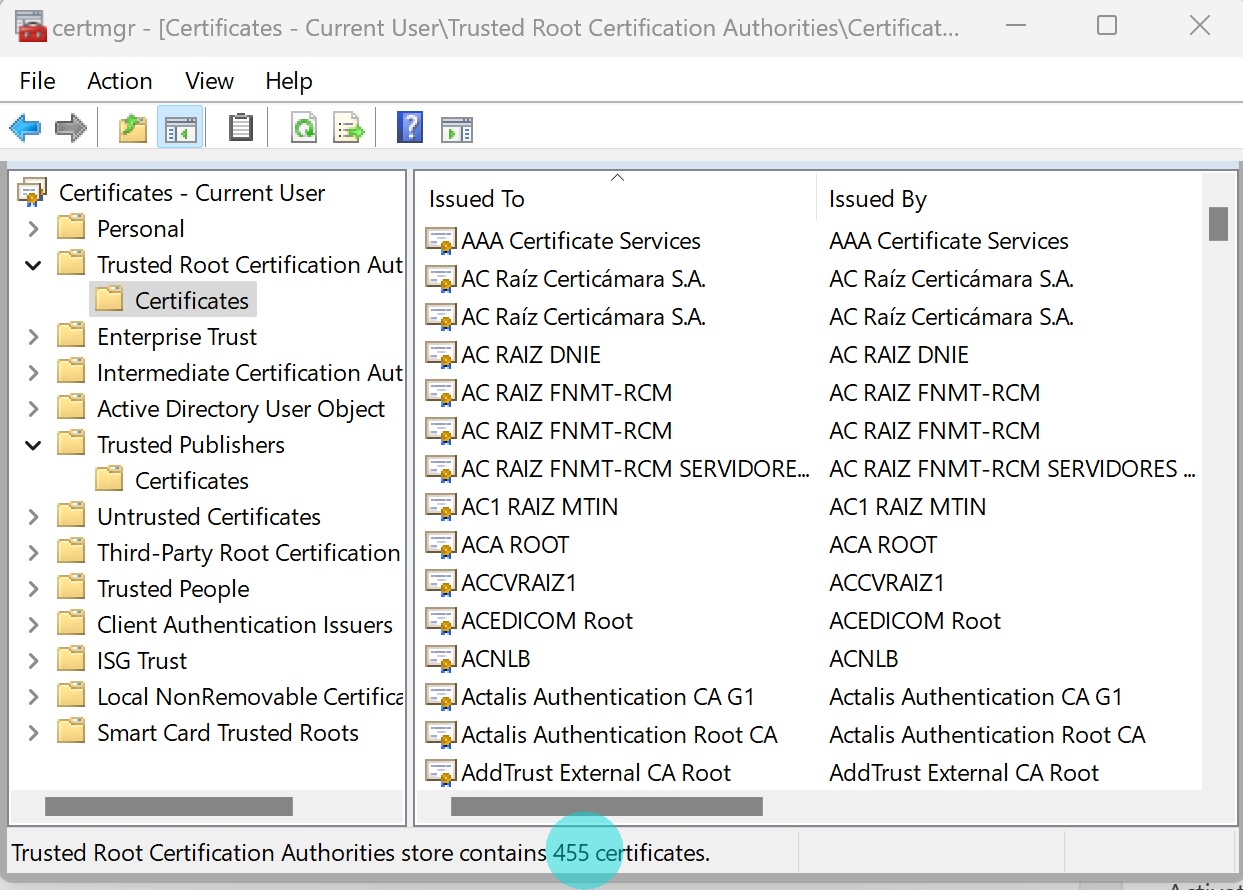
After that, the only thing left to do is to run the certmgr.msc snap-in and make sure that all certificates have been added to the Trusted Root Certification Authorities list. The list must contain much more certificates compared to the original one!
To Sum Up
Keeping your Windows servers up to date with the latest updates is crucial for maintaining the security and performance of your systems. By doing so, you can protect the customers' data from potential threats and ensure that the ecosystem runs smoothly. But, if the security levels in certain locations do not allow the CCTV system to be online, you must be aware of and apply the manual maintenance techniques.


